AML Vulnerabilities in Prime Broker
Preventing Money Laundering Through Automated Prime Brokerage Workflows
Critical Alert: Prime Brokerage Vulnerabilities Under Exploitation
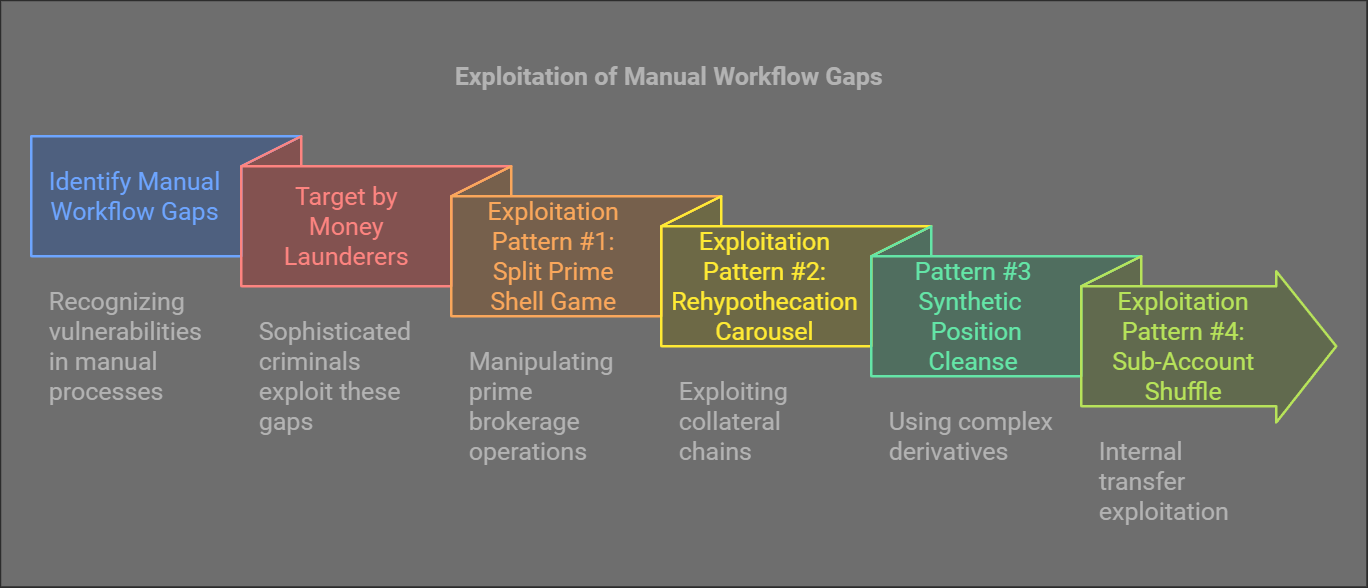
Manual workflow gaps in prime brokerage operations are being actively exploited by sophisticated money launderers. Our research has identified five major exploitation patterns that take advantage of workflow vulnerabilities.
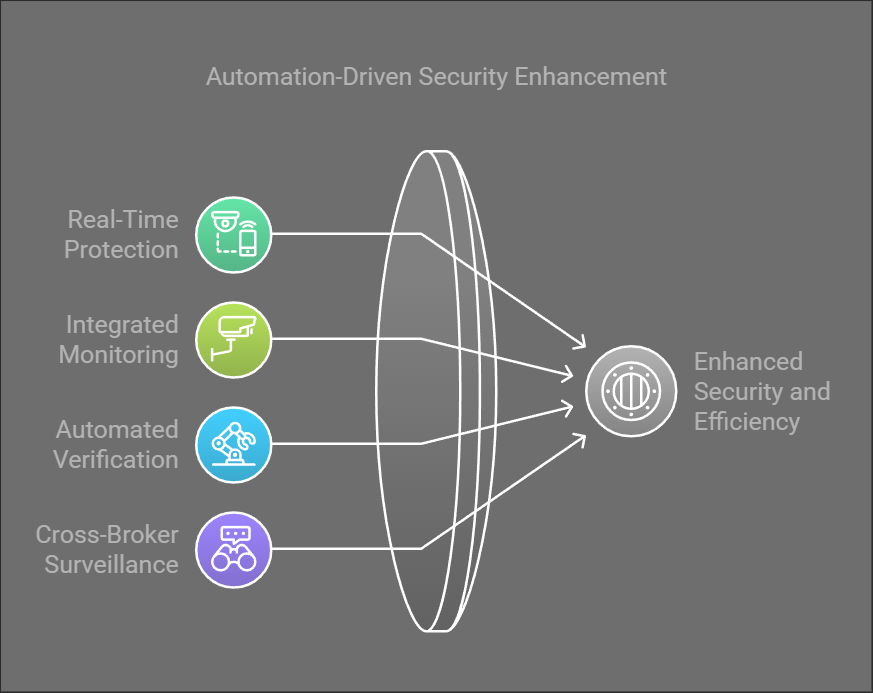
Automated Defense: Comprehensive Protection
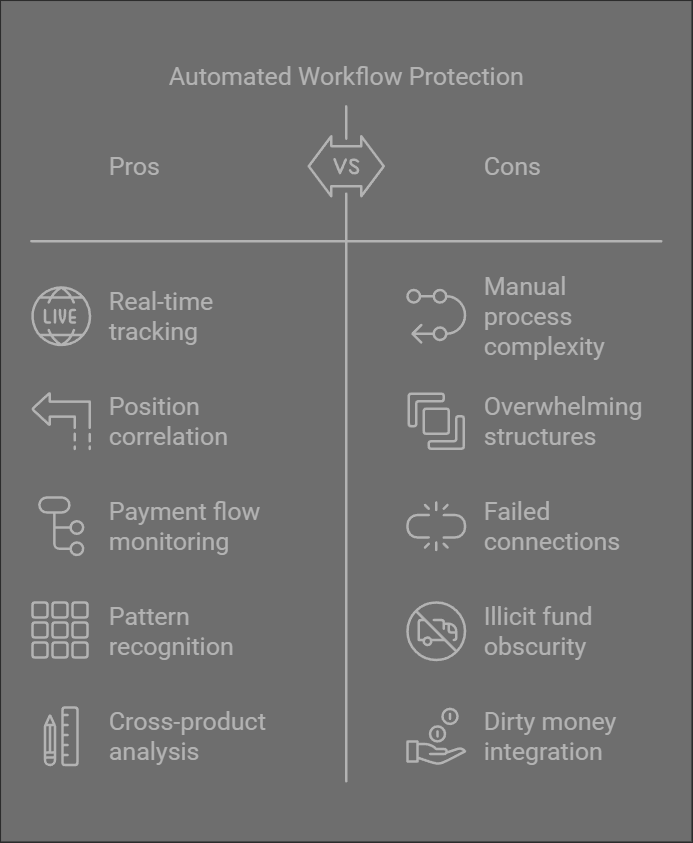
Our automated workflow solution provides real-time protection against these exploitation patterns through integrated monitoring, automated verification, and cross-broker surveillance.
Exploitation Pattern #1: The Split Prime Shell Game
How Bad Actors Exploit Manual Workflows
In this sophisticated scheme, money launderers exploit the lack of coordination between multiple prime brokers to obscure the movement of illicit funds:
Vulnerable Manual Process
-
- Bad actor establishes relationships with multiple prime brokers
- Creates complex network of nested offshore entities as sub-accounts
- Each prime broker only sees their portion of trading activity
- Manual compliance checks fail to connect related entities
- Trades between related entities appear legitimate in isolation
Protected Automated Workflow
-
- Automated entity relationship mapping across prime brokers
- Real-time monitoring of connected entity transactions
- Cross-broker activity surveillance
- Automated beneficial ownership verification
- Pattern detection across seemingly unrelated accounts
-
- Entity Relationship Mapping: Automatically identifies and tracks connections between entities across prime brokers
- Cross-Broker Surveillance: Monitors and correlates trading patterns across multiple prime relationships
- Automated Due Diligence: Consistent verification of complex ownership structures
Exploitation Pattern #2: The Rehypothecation Carousel
Exploiting Collateral Chains
This scheme exploits manual gaps in collateral tracking to layer illicit funds through complex lending chains:
Vulnerable Manual Process
-
- Bad actor posts questionable collateral at Prime Broker A
- Uses that collateral to borrow securities
- Pledges borrowed securities as collateral at Prime Broker B
- Creates circular chain of lending/borrowing
- Manual processes fail to track full collateral chain
Protected Automated Workflow
-
- Automated collateral verification and tracking
- Real-time monitoring of rehypothecation chains
- Integration with securities lending systems
- Automated detection of circular collateral arrangements
- Cross-broker collateral usage tracking
-
- Collateral Chain Tracking: Real-time visibility into complete rehypothecation chains
- Automated Verification: Immediate validation of collateral quality and source
- Pattern Detection: Identification of suspicious collateral movement patterns
![]()
Exploitation Pattern #3: The Synthetic Position Cleanse
Complex Derivatives Exploitation
This sophisticated scheme uses complex derivative positions to obscure the movement of illicit funds:
Vulnerable Manual Process
-
- Establishes complex derivative positions across multiple primes
- Creates offsetting positions that appear legitimate
- Introduces dirty money as “hedge” payments
- Manual processes fail to connect related positions
- Complex structures overwhelm manual review
Protected Automated Workflow
-
- Automated tracking of all derivative positions
- Real-time position correlation analysis
- Integrated payment flow monitoring
- Automated detection of suspicious hedging patterns
- Cross-product exposure analysis
-
- Position Correlation: Automated analysis of related positions across venues
- Payment Flow Monitoring: Real-time tracking of all related cash flows
- Pattern Recognition: Detection of suspicious trading and hedging patterns
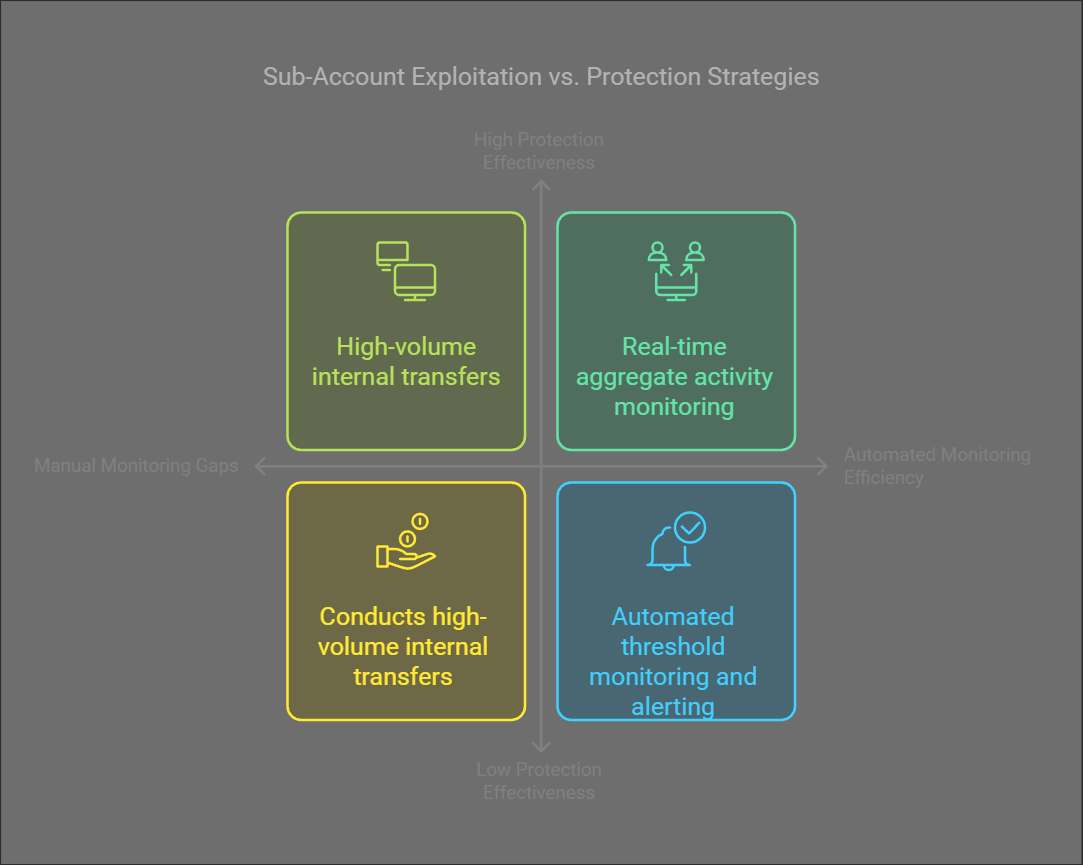
Exploitation Pattern #4: The Sub-Account Shuffle
Internal Transfer Exploitation
This scheme exploits manual monitoring gaps between sub-accounts to layer illicit funds:
Vulnerable Manual Process
-
- Opens numerous sub-accounts under different entities
- Conducts high-volume internal transfers
- Mixes legitimate and illegitimate funds
- Manual monitoring fails to track aggregate activity
- Reporting thresholds bypassed at sub-account level
Protected Automated Workflow
-
- Automated sub-account relationship mapping
- Real-time aggregate activity monitoring
- Integrated transfer pattern analysis
- Automated threshold monitoring across accounts
- Cross-account flow tracking
-
- Aggregate Monitoring: Real-time tracking of activity across all related accounts
- Pattern Analysis: Automated detection of suspicious transfer patterns
- Threshold Management: Cross-account threshold monitoring and alerting
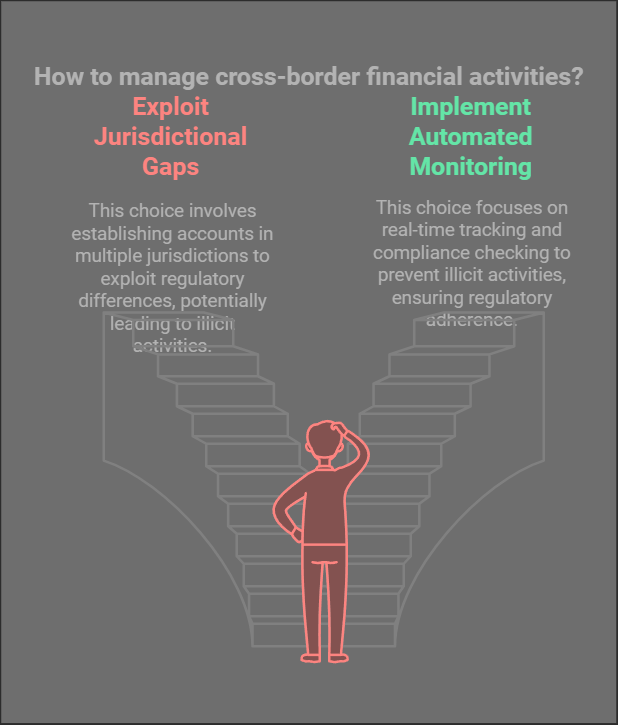
Exploitation Pattern #5: The Cross-Border Arbitrage
Jurisdictional Gap Exploitation
This scheme exploits gaps in cross-border monitoring to move illicit funds across jurisdictions:
Vulnerable Manual Process
-
- Establishes accounts in multiple jurisdictions
- Exploits time zone and regulatory differences
- Creates complex cross-border trades
- Manual processes fail to track cross-border flows
- Regulatory arbitrage opportunities exploited
Protected Automated Workflow
-
- Automated cross-border activity monitoring
- Real-time regulatory compliance checking
- Integrated multi-jurisdiction surveillance
- Automated suspicious pattern detection
- Cross-border flow tracking
-
- Cross-Border Monitoring: Real-time tracking of international transactions
- Regulatory Compliance: Automated checking against multiple jurisdictions
- Flow Analysis: Detection of suspicious cross-border patterns
Comprehensive Protection Through Automation
Our automated workflow solution provides integrated protection against all these exploitation patterns through:
- Real-Time Monitoring: Continuous surveillance across all prime brokerage activities
- Integrated Analysis: Correlation of activities across brokers, accounts, and jurisdictions
- Automated Verification: Consistent checking of entities, transactions, and patterns
- Complete Audit Trail: Full documentation of all workflow decisions and actions
Future-Proofing Your Operations
As money laundering techniques continue to evolve, our automated workflow solution adapts through:
- Regular updates to detection algorithms and patterns
- Configurable risk parameters and thresholds
- Integration with emerging compliance requirements
- Continuous monitoring and adaptation of protection measures